Updating and upgrading your Flipper Zero firmware
Spike F May 18, 2024Do you want to start unlocking the true power of your Flipper Zero? Well, good news! This is one of the many ways to do it, and possibly one of the easiest.
Updating your firmware
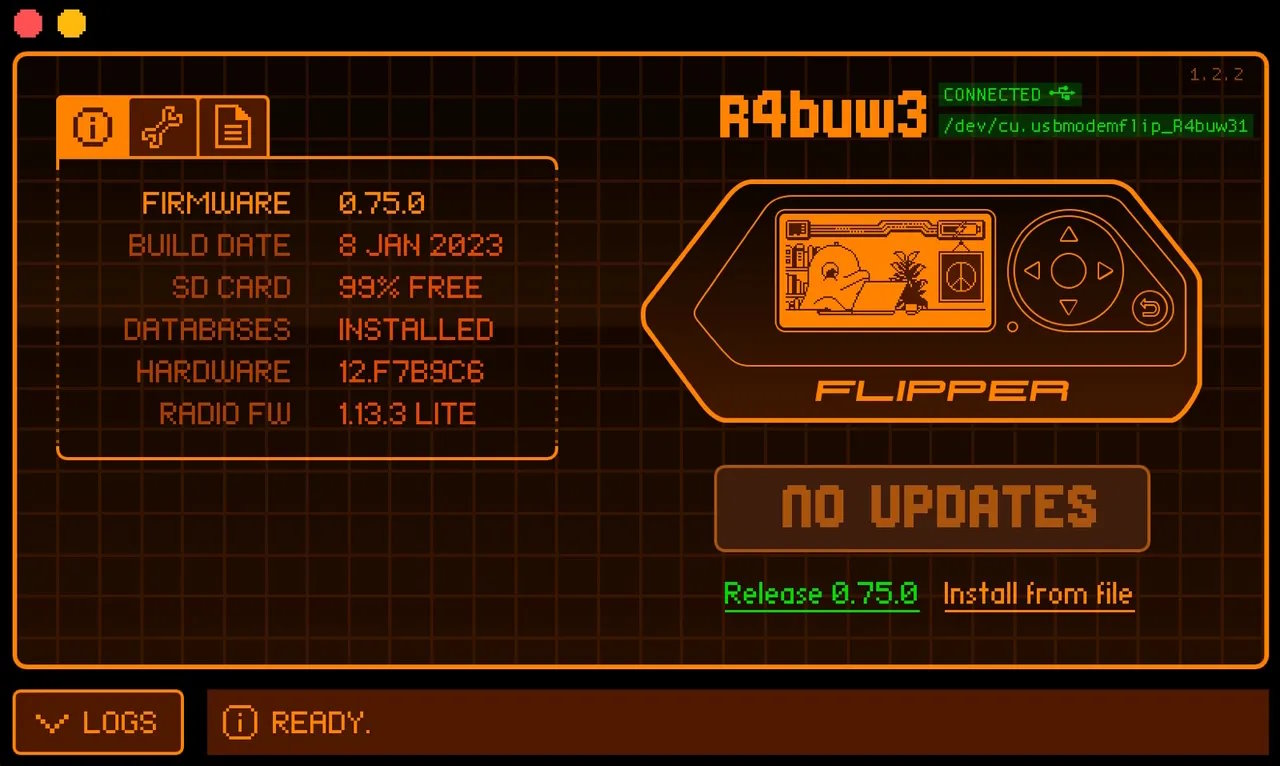
Download qFlipper
The first step is to download qFlipper. qFlipper is a desktop app used for updating the Flipper Zero firmware from your compute. You can download this form the Flipper Zero website.
You can then launch it from the command line using
chmod +x qFlipper-x86_64-1.3.3.AppImage
sudo ./qFlipper-x86_64-1.3.3.AppImage
This process ensures you have the latest security patches and features. Navigate to your Flipper Zero device's settings, find the "firmware update" section and follow the prompts. Your Flipper Zero will make the process fairly easy.
The Flipper Zero community is always working to build new updates and improve the software, so it's important you install any new firmware updates.

Modified firmware
Just like any truly limitless device should allow you to, you can install your own versions of firmware on to your Flipper Zero. Though the standard code installed on your Flipper Zero is fairly powerful, there are many new things you can do in order to advance it's power.
One of these examples if the RougeMaster firmware.
The Rouge Master's firmware for the Flipper Zero is a complete modification that adds an array of community projects, all with no pay wall.
It's actively being updated and improved on each day by the Flipper Zero community, and it's supported by RM Pro and Patreon backers. This is part of the reason why we at techbites.co.uk would recommend this as a great piece of custom firmware to test out!
The latest update to the RougeMaster firmware includes enchancements to the Flipper Zero ESP32 WiFi devboard module as well as the J305 Geiger Counter, Camera Suite and fun new mini games like "Yappy Invaders".
Alternative custom firmware
There are many other versions of Flipper Zero customer firmware, with two earning an honorable mention in this post.
Please do your own research on these firmware versions - we do not have any associate with the above firmwares, or RougeMaster firmware.
Installing your firmware
Important things to remember before you begin
- Ensure your device has been updated to the latest official firmware before you begin.
- If you're already using unleashed firmware, you can install the latest version on top of your current device without any additional steps.
- Verify you have a microSD card installed in your Flipper Zero.
Installing using qFlipper (1.2.0+)
- Download the latest version of qFlipper - this will allow you to install the .tgz file that makes up the firmware.
- Open latest release page
- Download the latest version
- Launch qFlipper
- Connect your device and select Install from file
- Select the .tgz file that you downloaded
- Update should begin
- Wait for it to complete
- If all has been done successfully, you will have your new firmware ready to play around with!
Adding hacks to your Flipper Zero
After updating to custom firmware, you are ready to get in to the most exciting aspect of owning a Flipper Zero - adding and using hacking tools!
How to add hacks to your Flipper Zero
- Choose Your Hack: Begin by selecting a project or hack that catches your interest. Ensure that it's compatible with the latest firmware version of your Flipper Zero and take the time to go through any documentation provided by the creator.
- Download and Transfer: Next, download the necessary files onto your computer. Connect your Flipper Zero to your computer using a USB cable and transfer the files to the appropriate directory on the device. This typically involves copying files to the 'flipper' directory.
- Installation and Activation: Depending on the hack, there may be specific installation steps involved. This could include running scripts through the Flipper Zero's interface or other procedures. Follow the instructions provided for the hack you're adding. Make sure to grasp each step to prevent unintended modifications to your device.
- Testing: After installation, it's essential to test the hack in a controlled and legal environment. Remember, the aim is to learn and explore technology ethically.
The Flipper Zero serves as a versatile multi-tool for hackers, integrating several key components that facilitate a wide range of interactions with electronic devices. Below is an overview of its main components and the potential hacks or interactions enabled by each one.
Radio Frequency (RF) Transceiver
Capabilities: The RF Transceiver boasts a wide spectrum of frequencies, facilitating communication with devices utilizing RF protocols such as RFID, NFC, and Sub-GHz frequencies.
Potential Hacks: This component opens doors to various hacks, including cloning RFID tags for access control systems, analyzing and replaying signals from car key fobs, or engaging with wireless doorbells and remote controls. Its versatility makes it a robust tool for both exploring and exploiting vulnerabilities within RF-based systems.
Infrared (IR) Transmitter/Receiver
Capabilities: Equipped with the ability to send and receive IR signals, akin to those employed by remote controls for TVs, air conditioners, and other IR-based household electronics.
Potential Hacks: With the IR Transmitter/Receiver, possibilities abound. You can clone and dispatch IR commands to control a multitude of devices, craft universal remotes, or automate the management of IR-based smart home appliances.
Flipper-IRDB: This additional resource enhances the Flipper Zero's capabilities in the IR realm, providing a comprehensive database to further streamline interactions with IR-based devices.
Bluetooth Low Energy (BLE) Module
Capabilities: Enables communication between your Flipper Zero and your other BLE devices, which are prevalent in modern smart devices, wearables, and IoT gadgets.
Potential Hacks: Sniffing and analyzing BLE signals to discover vulnerabilities, spoofing BLE devices, and interacting with smart locks or fitness trackers. There is so much potential when using your Flipper Zero to interact with BLE devices.
USB Interface
Capabilities: Your Flipper Zero can act as a USB device or host, which means it can directly connect to computers and other USB compatible firmware.
Potential hacks: You can use the USB interface on your Flipper Zero to emulate keyboards, mice or execute automated commands on the connected computer (Known as BadUSB attacks). Injecting malicious code and exfiltrating data are also ways you can use the device to your advantage.
GPIO Pins
Capabilities: General Purpose Input/Output pins can be used for low-level interaction with electronic circuits, sensors, and other devices. The GPIO pins can also be used to connect the Flipper Zero ESP32 WiFi Devboard.
Potential Hacks: Creating custom electronic projects, interfacing with custom hardware, automating physical processes, or reverse engineering device protocols. When connected to the WiFi devboard, you can also use the device to create fake WiFi portals.
Creating fake WiFi portals
There are two main third party tools you can use to create fake WiFi portals with your Flipper Zero:
iButton Reader
Capabilities: The iButton reader can be used to interact with iButton devices, which are used in some access control and identification systems.
Potential Hacks: Cloning iButton tokens for access control bypass and auditing security systems that utilize iButton for physical access.
Useful software
The iButton Fuzzer plugin is a great plugin for your Flipper Zero that is made for the Flipper Zero Unleashed Firmware. It also works on the original firmware. It supports the protocols DS1990, Metakom and Cyfral.
NFC (Near Field Communication) Module
Capabilities: The NFC module on the Flipper Zero enables it to communicate wirelessly with devices over fairly short distances (typically a few centimeters). It’s designed for contactless interactions, such as data exchange, access control, and payment transactions.
Potential hacks:
- Cloning Access Cards: By copying the data from an NFC-based access card, users can create duplicates to gain entry to secured locations.
- Data Sniffing: Intercepting and analyzing NFC communications can reveal vulnerabilities or sensitive information transmitted in clear text.
- Automating Malicious Tasks: Programming NFC tags to direct smartphones to malicious URLs or to execute harmful actions when read.
Useful software
You may find it useful to take a look at this GitHub repo, which is a collection of helpful information for use with your Flipper Zero.
Sub-GHz Module
Capabilities: The Sub-GHz module supports communication over frequencies below 1 GHz. It’s utilized in a variety of devices, including remote controls, automotive key fobs, and some wireless communication systems. You can use your Flipper Zero to clone keyfobs.
Potential Hacks: Duplicating signals from devices like garage door openers or vehicle key fobs to control them without the original remote. Analyze security systems and test the security of wireless alarm systems that operate on Sub-GHz frequencies to find potential exploits.
You can also capture and decode Sub-GHz transmissions to reverse engineer the communication protocols of various devices, aiding in the discovery of new hacking techniques or vulnerabilities.
Conclusion
In conclusion, the Flipper Zero can be used in so many different ways. We highly recommend installing custom firmware for your device as this will unlock the full potential of the Flipper Zero.
If you would like to know more about your device, feel free to reach out. We at techbites pride ourselves on our passion for technology.
The Flipper Zero and Flipper Zero WiFi devboard are both available for purchase on our website at the cheapest prices in the UK, with free next day delivery.